How heylogin protects your employees from phishing

Every year, the number of cyberattacks on companies increases worldwide. In Germany alone, companies suffered losses of 200 million euros last year.
Phishing is the most common means used by criminals to obtain employees' access data.
Targeted training is one way to prepare employees for such attacks. However, it is better to use software to render a few of the regular phishing methods ineffective from the outset.
Phishing via fake email
Phishing emails have many faces: some are so obviously fake that even untrained personnel won't fall for them (for example, spelling mistakes and incorrect grammar, false names, etc.). Others, however, are perfectly tailored for use against their employees.

These phishing emails have a good chance of success, both with untrained personnel such as interns and with less technically skilled employees. With heylogin you can make such attacks ineffective directly.
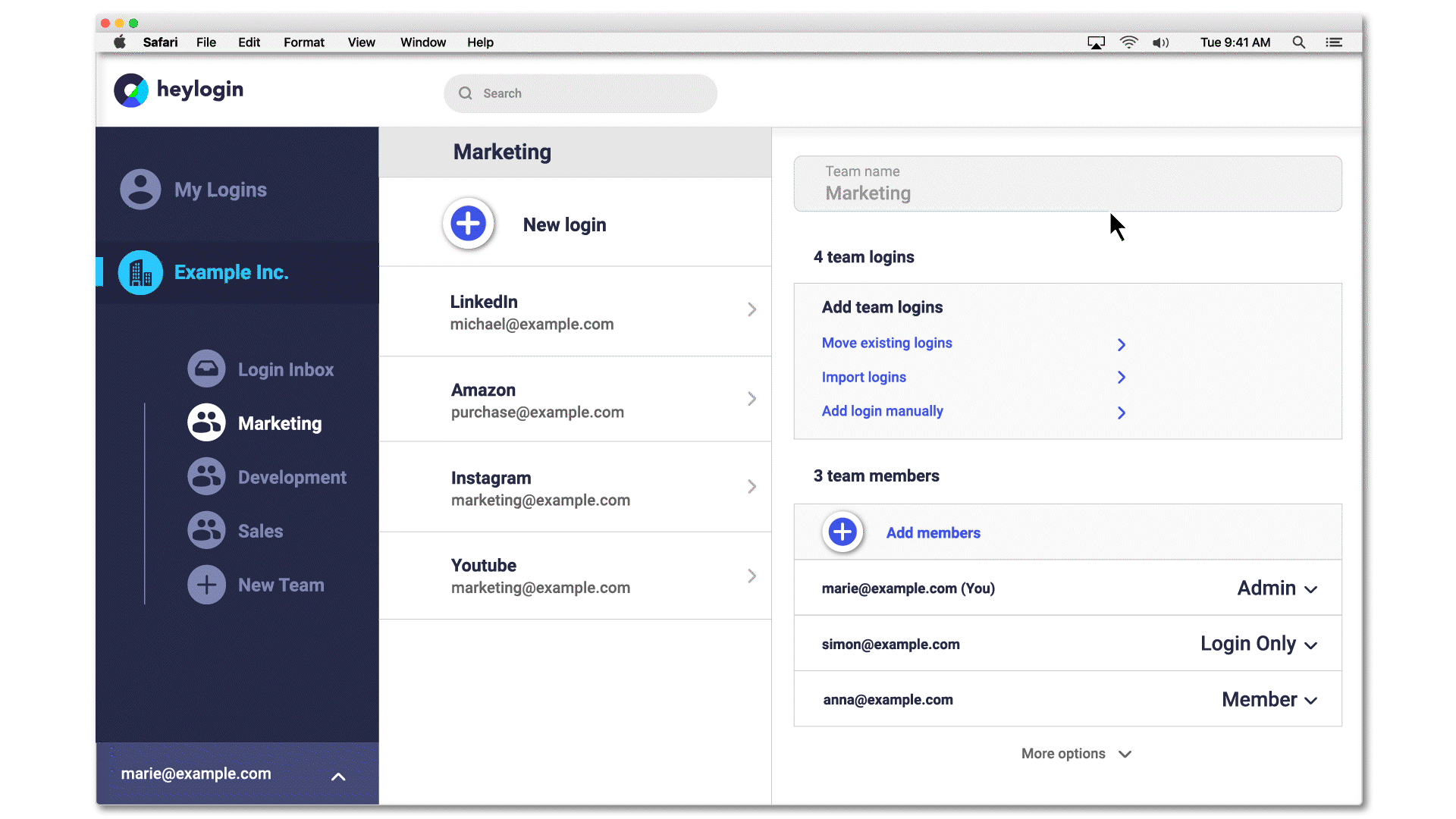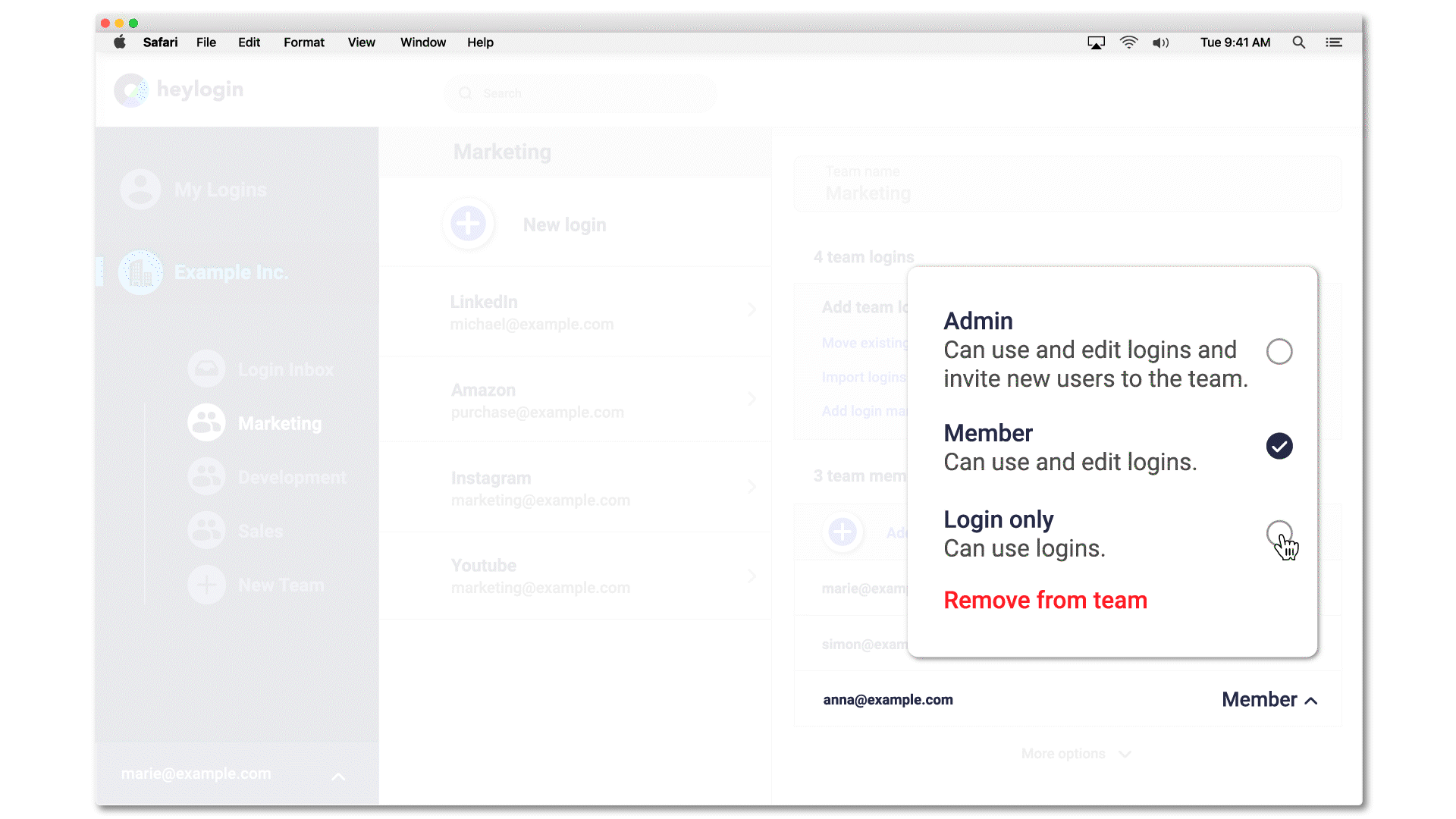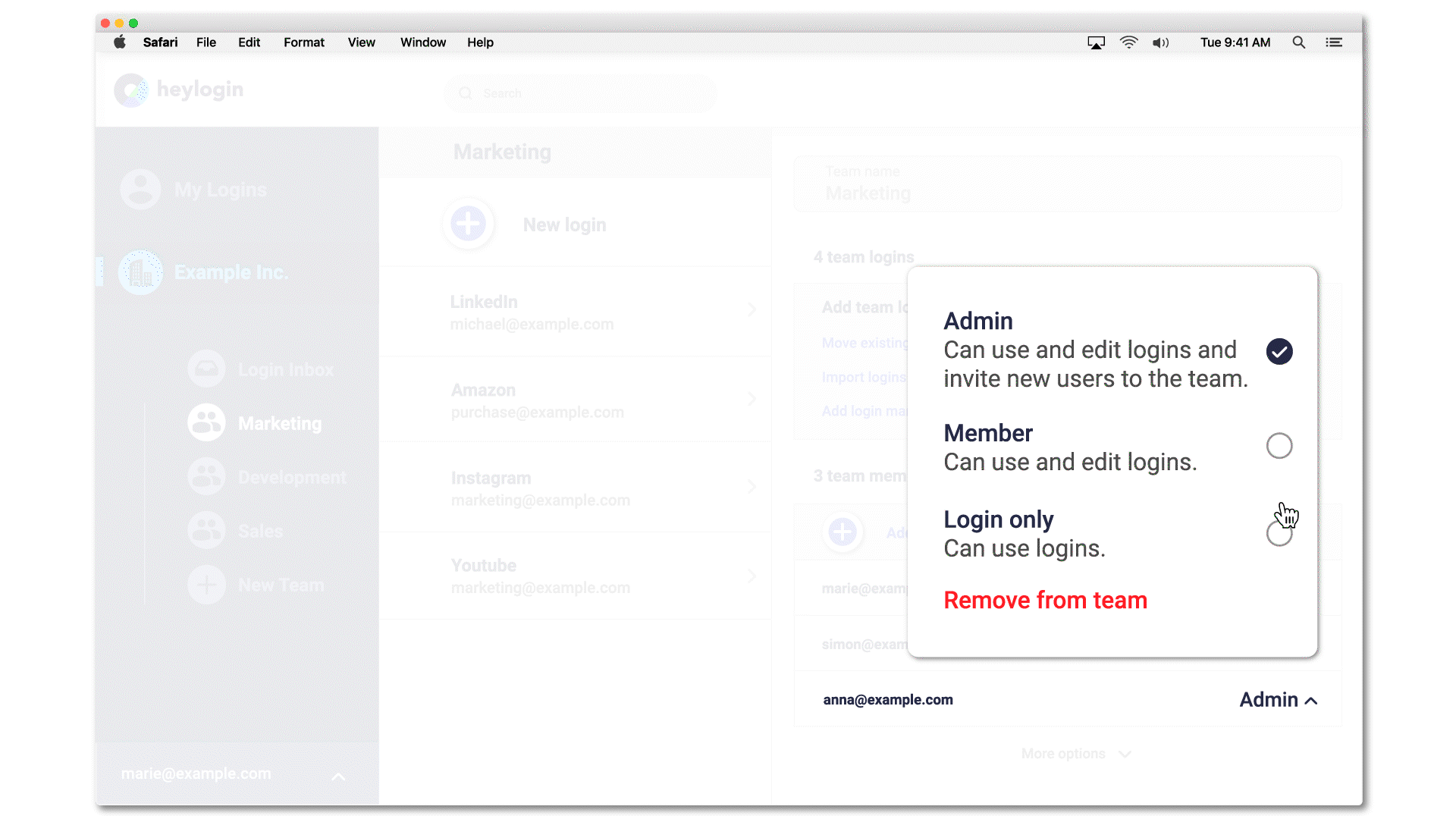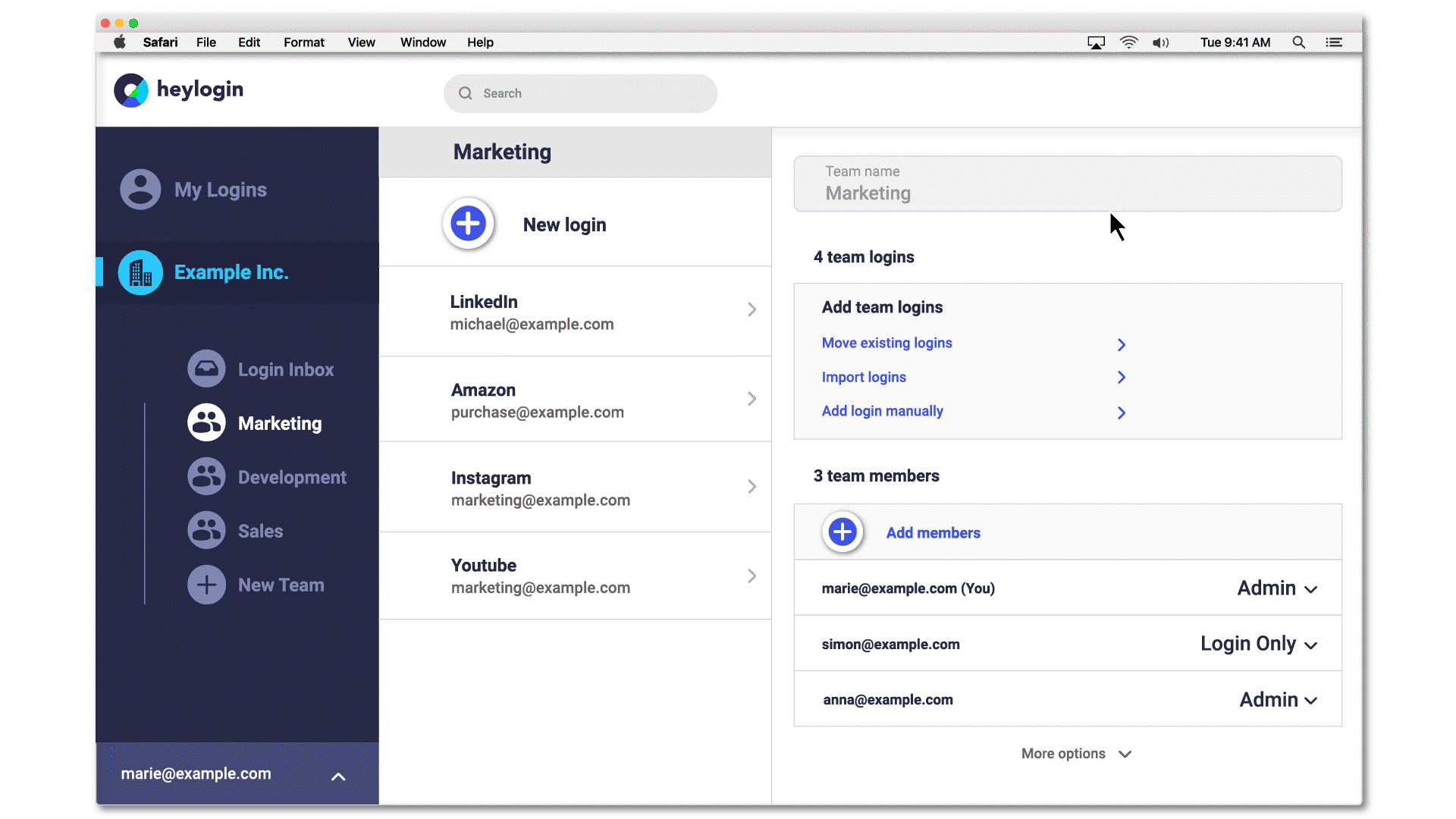
Access to passwords can be restricted by setting permissions. The setting "Login only", for example, only allows to use the login, i.e. to log in on a page via 1-click overlay. The password is invisible, both in heylogin itself and when logging in. If a password isn't know it can't be shared by mistake.
Additionally, all actions that involve sharing or editing logins can be easily done in the heylogin web app. If an admin really needs access, the login only needs to be shared in a newly created team, all securely encrypted with modern algorithms.
Phishing via fake website
Another phishing variant redirects via email link to a deceptively real website where you are supposed to enter your login data. For example, you receive an e-mail from Amazon, but the e-mail address looks a bit strange. You didn’t notice, click on the link to the fake page and are then asked to log in.

Without software you enter your data and the damage is done, but with heylogin this does not happen. The 1-click login only appears on websites for which a login is explicitly stored in heylogin. Your Amazon login will only appear on the real Amazon page, so the fake will be unmasked directly.
Other phishing methods
Of course, there are other types of phishing, and even heylogin does not protect against all of them. In case of email attachments and links that install malware, even a password manager won't help. This malware usually has system access or can access or store data outside the encrypted password manager system through technical means.
That's why you should use heylogin
So heylogin is not an ultimate protection against phishing, but that doesn't mean you are better off without it. Humans are the biggest source of mistakes and the first point of attack for criminals.

By using software like heylogin, you take the burden off your employees:
- permissions prevent the accidental release of passwords
- logging in to a website can only be done with heylogin, if a login for this website has been explicitly defined
- passwords can be easily managed in heylogin and are always securely encrypted
Try us out and enjoy other benefits like easy 1-click login, smartphone confirmation via swipe instead of password and simplified 2-factor authentication for your most important websites. There are also several articles on the latter in our blog ;)
